Recently as I was helping out a friend, he was struggling with port forward on his router. Well after we discovered why was this an issue… oh boi. So the selected TCP port was 8200 for some reason and on the same port on the public side of the router, the port was occupied by an old NAS. Nevertheless the router was 5+ years old as well. This port was a miniDLNA host, which was only supposed to be on the local network for general media-consuming devices.
This brings a few issues and problems. First of all, anyone from outside without authentication could potentially see how many files, each media library with a simple HTTP connection to this port. The output would be something like this:
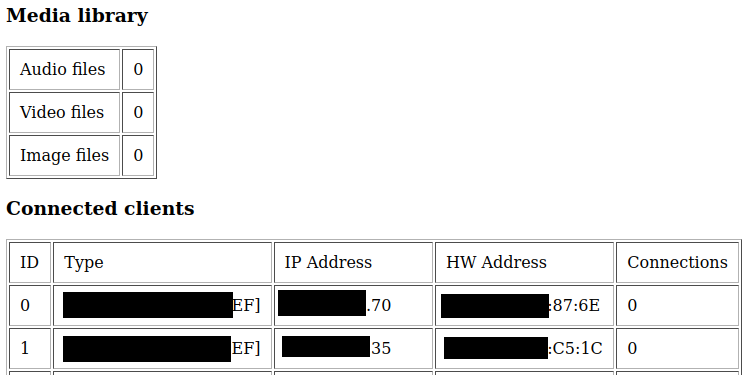
And as you can see even the client type (based on Mac address), client IP address and the mac address of the device leak out. That is no good indeed. However later on I looked into the DLNA protocol which is an extension of the UPNP protocol. UPNP protocol is in itself a massive topic. So in this article, I will only focus on the DLNA-specific parts and especially look into the miniDLNA service, which has a common misconfiguration issue. And the whole issue here is not the MiniDLNA itself, but the combination of a modem router, which is implemented without security in mind, which would without question expose this service to the public. In our case I have done quick research on shodan how many miniDLNA boxes available for anyone on the internet.
~50,000+ listed on shodan. Mostly these are ISP-provided routers and Home Nas solutions, but they are empty. These are only exposed due to bad default settings on devices. It’s hard to filter out these empty ones, however during this research, I found a fair few with content.
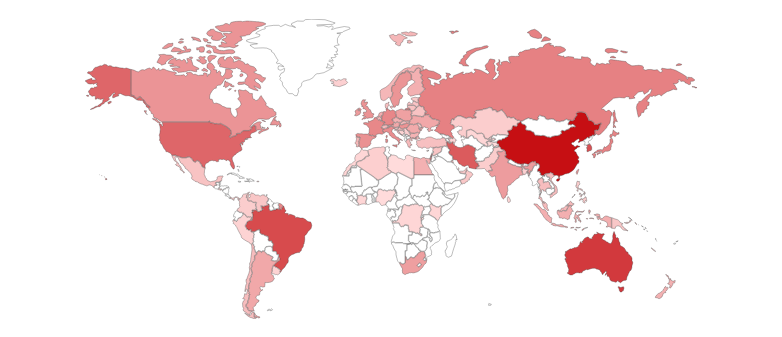
The really big issue comes now. We have a family (probably non-technical, but seen otherwise) who wants to share content on a smartTV / Gaming console. DLNA is the first choice. So they purchase a NAS or run a server from their PC. Most NAS these days are fine(better practice, security patches), but the older ones got some issues. In our case, these old NAS and self-hosted services have one in common which is misconfiguration issues. Which will result in exposed service as the modem router when it receives the DLNA server UPNP SOAP actions to help the discovery of the services for other local network devices. The modem router will expose it for some messed up reason, hence we have these boxes on the internet. From now on YOUR DLNA SERVER, will be

After looking at the SOAP actions. I was able to write a small scanner script, which would list all available content names, metadata (if available) and an URL, where you can download this content. If anyone were to look on these servers, they would find CCTV footage, Phone/Camera galleries, Downloaded movies, Scanned documents and a lot more.
I even tried to report it to the authorities, however they could not do anything with it and it’s somewhat a legal grey zone, as ISPs have no baseline standard for devices (which is the bigger issue in my opinion) and the authorities have nothing to do if someone uses an out-dated our badly configured device of course.
The mitigation I can recommend for users who using these DLNA services is this. Disable DLNA at all costs. Try testing other solutions. For content delivery recently I can recommend Plex, Jellyfin or Emby. Depending on your media content consumer device, you might get away with something like SMB(v3 only). Regarding modem routers, there is nothing we can do with them, the only solution is possibly spend decent money we could potentially purchase a modem router from some big brand, but finding a good one among those is still challenging. Choosing a device like this can be a pain in the bacon, even for a tech-savvy person.