write up : Link to heading
Prologue Link to heading
I made this challenge as an introduction to IOT micropython and MQTT as well to spread the word that these are good platforms for some use-cases. For the first challenge basically to read some documentation, and see whats happening when these are not really updated or the application not compiled with good presets for your platform. The second part of the challange is mostly about finding already written modules and how to connect to MQTT and what to look for. This is a bad, basic example as it’s only uses credentials as authentication and the connection not even encrypted. The third challenge is a bit more guessy. It was just a meant to be for those whom looking for anomalies not just for flags :D
tiny_sneak_1 Link to heading
First lets telnet into box: telnet /nc to ip 2220
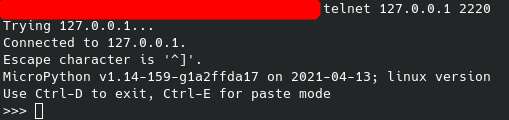
So this is a micropython linux build. After a bit of search we will find this documentation. In the documentation there are lots of interesting functions, however even most of the functions are not implemented in this build. Because the linux build of the micropython most of time not tested. And the default compile settings are really minimal. So let’s go for a walk. As we know now thanks to the website it’s a python3.7 port like binary which was created for iot devices. So the syntax will be familiar only function and modul names are different. So to look around we need look trough file system. Which in normal case is os.listdir(), but in our case this function does not exist just only ilistdir which is a bit different, but still the same, as its gives you back a list.
for i in uos.ilistdir():
print(i)
This will list our directory which is the root directory and there will be a file called flag So we just need to print it with
open("/flag9ab17b822020c7cce76295ffb78cb7e15358074e5b7e5fe58db2a22644b27098").read()
ctf{my_pyth0n_1s_k1nd4_m1cr0}
Boom we have flag for snake
tiny_sneak_2 Link to heading
Next there is a clue that there is something I worked on. So if we look around there are fishy directories and files, but we have only read permission for /test let’s see what’s inside. There is some other way to find it for example.
import usys
usys.path
['', '/data/.micropython/lib', '/test']
It’s a file called sub.py So let’s print it.
r = open("/test/sub.py")
r.read()
import time
from umqtt.simple import MQTTClient
import random
# sub test know i can see all of my topics
# Received messages from subscriptions will be delivered to this callback
def sub_cb(topic, msg):
print((topic, msg))
def do_sub(topic="", server="127.0.0.1", user="sensors", password="hunter2",port=1833):
c = MQTTClient(str(random.randint(1,1000000)), server,user=user,password=password,port=port)
c.set_callback(sub_cb)
c.connect()
topic = topic.encode()
try:
c.subscribe(topic)
while True:
if True:
# Blocking wait for message
c.wait_msg()
else:
# Non-blocking wait for message
c.check_msg()
# Then need to sleep to avoid 100% CPU usage (in a real app other useful actions would be performed instead)
time.sleep(1)
except:
print("give at least one topic")
c.disconnect()
As we see it’s a Mqtt client which contains creds and connection details sweet. So let’s connect to it we could use mp our own client which ever works. I am using for the sake of argument MQTTX. At this point you should familiar yourself with mqtt which is a topic based communication service for design to embeddedd systems. So we need to see all the topics to see what’s important so we will subscribe to # which means every topic and oh boi so much line so after we waited we can try to search the lines for a string containing flag and boom we found our flag for this sucks
Topic: CPVMo6lfSGtth0J1mHaqRMvsbO0hpsRsQoS: 0
ctf{mqtt_h4s_s0m3_1nt3r3st1ng_4ngl3}
tiny_sneak_3 Link to heading
But hey there is one line which does not make sense
Topic: /web/status/server.local
200
That’s indicate there is a web server and we have no idea how to connect to it on our what port, because only mqtt port is public. Hmmm but we a mp debug we could use that for the connection. Well the hint says we have all the information and module we need so what would be the way to get http well requests module. So if we follow the naming pattern we have urequests so
import urequests
r = urequests.get("http://server.local")
r.text
'ctf{h1dd3n_fl4g_t3ll_n0_0n3}'

And we have our third and last flag in this challenge series